This is the
age of silicon ![]() .
.
Surviving the information wars requires digital fortification.
Computer
system security ![]() and
network security
and
network security ![]() are necessary for the protection of sensitive data.
are necessary for the protection of sensitive data.
We implement
local area network ![]() (LAN) and cloud security packages that ensure data safety.
(LAN) and cloud security packages that ensure data safety.
Business-class
hardware ![]() provides the infrastructure and
provides the infrastructure and
trusted, proven
security suites ![]() handle data access and encryption.
handle data access and encryption.
Don't be the next newsworthy data breach ![]() .
.
Hackers ![]() live to snack on your
bits
live to snack on your
bits ![]() and
bytes
and
bytes ![]() .
.
Sensitive documents, customer information, emails, and trade secrets must remain off their plates.
Viruses ![]() ,
malware
,
malware ![]() ,
trojans
,
trojans ![]() ,
spyware
,
spyware ![]() ,
spear phishing
,
spear phishing ![]() ,
and
ransomware
,
and
ransomware ![]() are just tastes of their malice.
are just tastes of their malice.
We implement and configure a variety of software security suites.
Drive encryption and
antivirus ![]() are only the hors d'oeuvres.
are only the hors d'oeuvres.
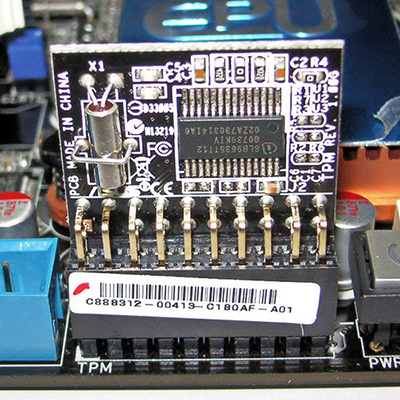
The handy little device in the picture is a
Trusted Platform Module ![]() chip.
chip.
It operates as excellent
endpoint protection ![]() through the use of a secure key-generating
cryptoprocessor
through the use of a secure key-generating
cryptoprocessor ![]() .
.
All personal and other sensitive data are encrypted through generation of
cryptographic keys ![]() and a series of other processes.
and a series of other processes.
Specifications for TPM were conceived by the
Trusted Computing Group (TCG)
![]() .
.
It could be any passing email.
Attached with an invoice from a trusted vendor.
Upon opening, the layout seems... unfamiliar.
The invoice file executes a link and downloads a
malware
![]() payload silently in the background.
payload silently in the background.
A
spear phishing
![]() attack succeeds and a device is compromised, as a result.
attack succeeds and a device is compromised, as a result.
The malware is free to take over systems and corrupt any data it pleases.
Data security
It's necessary to ward off the variety of attempts that scammers and hackers
Implementing endpoint protection
Priority Data Services
We make your data security our priority.
Cloud management
Recommended
Security Apps
Even with great
endpoint protection ![]() on all devices,
hackers
on all devices,
hackers ![]() will find a way to infiltrate.
will find a way to infiltrate.
Unsecured network systems are their buffets of choice.
Managed
routers ![]() with
firewalls
with
firewalls ![]() and
unified threat management
and
unified threat management ![]() devices (UTMs) outfitted with
security applications
devices (UTMs) outfitted with
security applications ![]() take you off the menu.
take you off the menu.
We are experienced in network hardware and UTM appliance installation and configuration.
Let's ensure your network connections, storage access, and throughput of data only get seen by who it's supposed to.
This innocuous little box looks like a common household
router ![]() .
.
In reality, a
framework ![]() is housed inside for running highly secure applications with up-to-the-minute threat recognition.
is housed inside for running highly secure applications with up-to-the-minute threat recognition.
Unified Threat Management ![]() devices are nearly impenetrable because they run on their own secure
OS
devices are nearly impenetrable because they run on their own secure
OS ![]() with a contained application environment.
with a contained application environment.
If you are serious about
hardening ![]() your network security, a UTM is the way to accomplish it.
your network security, a UTM is the way to accomplish it.
Prevent network intrusions, stop threats before they execute, and easily pass any security audits.
Check the
software section ![]() for information on the types of security applications that are available.
for information on the types of security applications that are available.
Managed
routers ![]() are a basic piece of network security hardware.
are a basic piece of network security hardware.
They include secure
firewalls ![]() that protect wired and wireless connections.
that protect wired and wireless connections.
Many models include the base framework for
VLANs ![]() and
VPN
and
VPN ![]() access.
access.
They are a great first stepping stone to complete network protection.
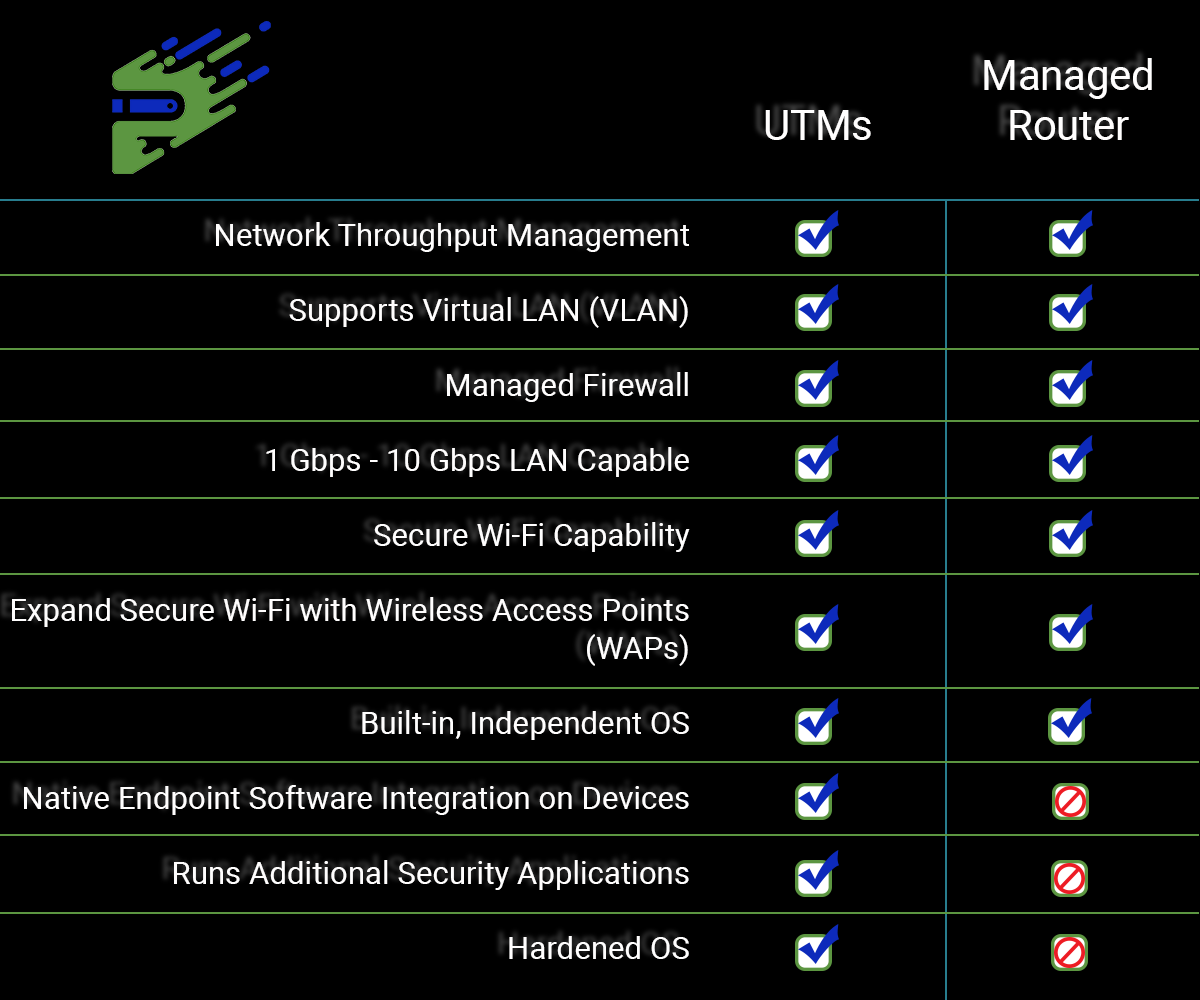
Physically, managed routers are nearly identical to a UTM appliance or household router.
Internally, a UTM
Please see the checklist for a brief comparison between them.
Security applications for networks are not far off from endpoint security.
The primary benefit of network security is that a majority of threats are headed off at the pass.
It comes with the added choices of content filtering ![]() ,
cloud antivirus
,
cloud antivirus ![]() ,
intrustion detection systems
,
intrustion detection systems ![]() ,
& more.
,
& more.
Applications for network security also create standardized policy and protections across all devices connected to that network.
These protections extend across
wired ![]() ,
wireless
,
wireless ![]() ,
and
VPN
,
and
VPN ![]() connections.
connections.
Advanced hardware/software combinations allow for separate policies to be enacted across multiple networks.
Click the button below for more information.

Adobe ![]() .
Zynga
.
Zynga ![]() .
eBay
.
eBay ![]() .
Yahoo
.
Yahoo ![]() .
Equifax
.
Equifax ![]() .
.
Each of these companies has a common denominator that they would love for all of us to forget about.
They allowed their customer's personal data to go unmonitored, be exposed, and potentially exploited.
Data breaches ![]() are a serious issue in the
age of computing
are a serious issue in the
age of computing ![]() .
.
Information leaked into the hands of
hackers ![]() is fair game to the highest bidders.
is fair game to the highest bidders.
In the wake of these attacks, new software and protocols have been developed.
Potential compromises can now be identified, stopped, and patched.
Stop security breaches and protect your customers' data and keep their confidence.
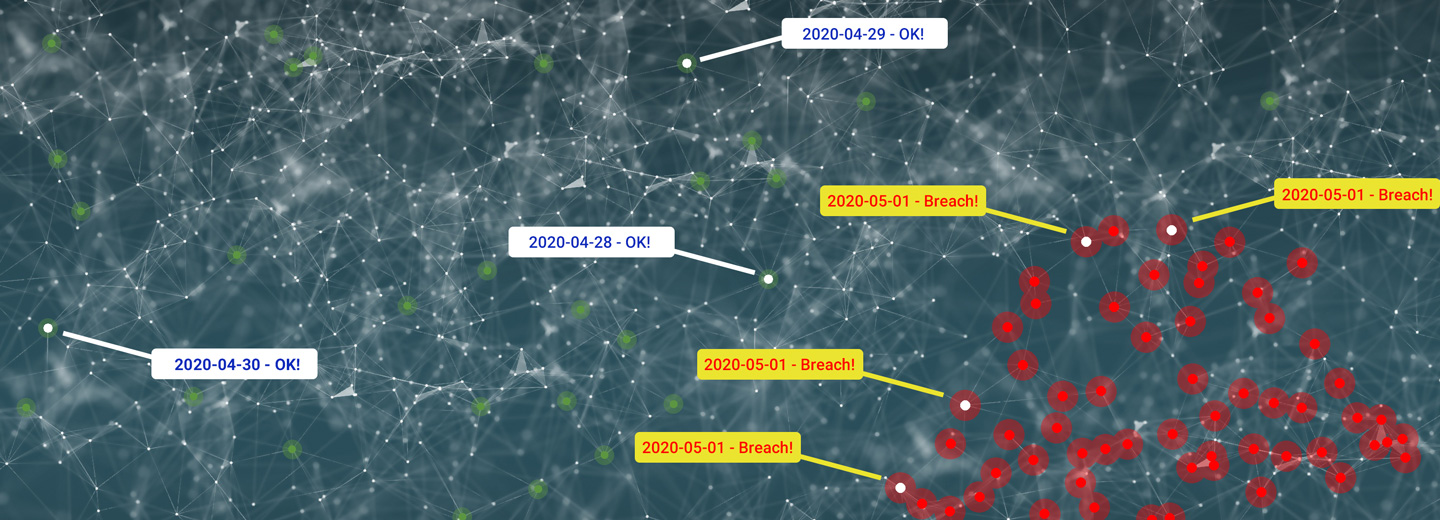
The top priority for sensitive data systems is that they need to be designed to prevent outside intrusions.
Much of this is mitigated by running proper
security hardware ![]() and combining it with both
endpoint
and combining it with both
endpoint ![]() and
network secuity
and
network secuity ![]() suites.
suites.
But what of the sophisticated hacker? Or intrusion within the system's network?
These, too, can be issues of the past.
Modern
data loss prevention software ![]() incorporates a bevy of additional
fail-safes
incorporates a bevy of additional
fail-safes ![]() .
.
Files can be marked for monitoring and provide warnings when accessed during unusual times or by incorrect credentials.
Internal leaks get stopped by locking out data to transfer to
flash drives ![]() ,
external storage
,
external storage ![]() ,
or email programs.
,
or email programs.
These and other methods are precisely executed by policy creation through
machine learning ![]() .
.
No more h4x0rs. No more disgruntled employees. No more embarrassing public apologies.